Cyber Attacks on the Power Grid

This confidential alert was sent to U.S. energy firms and their security consultants.
Imagine that one day you wake up and trading is halted on the New York Stock Exchange (NYSE) floor; meanwhile systems at United Airlines and the Wall Street Journal newspaper appear out of order.
It is not a scene from a movie; it happened on July 8, when trading at the NYSE stopped around 11:30 a.m. ET.
According the media, the temporary interruption of the services mentioned was a coincidence and the events are unrelated, but the incidents have raised once again the question of the real security of critical infrastructure.
White House spokesperson Josh Earnest confirmed that the incidents weren’t caused by cyber-attacks.
“It appears from what we know at this stage that the malfunctions at United and at the stock exchange were not the result of any nefarious actor,” said Department of Homeland Security Secretary Jeh Johnson. “We know less about the Wall Street Journal at this point except that their system is back up again as is the United Airline system.”
The Stock Exchange, transportation, and media are critical to the infrastructure of a country. A contemporary failure of these systems could cause serious problems to the nation, especially when the incident is caused by a cyber-attack.
Thus far, the temporary outage at the New York Stock Exchange, United Airlines and the Wall Street Journal’s website were the results of tech glitches, but we have to consider the US infrastructure remains vulnerable to cyber-attacks that would cause serious problems and would be costly.
To compound the scenario, there is the rapid increase in the number of cyber-attacks, at least of those we fail to detect, and its complexity.
The DHS’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) has issued its new ICS-CERT MONITOR report related to the period September 2014 – February 2015.
According to the report, the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) received and responded to 245 incidents in Fiscal Year 2014, more than half of the incidents reported by asset owners and industry partners involved sophisticated APT. ICS/SCADA system were also targeted by other categories of threat actors, including cyber criminals, insider threats and hacktivists.
“Of the total number of incidents reported to ICS-CERT, roughly 55 percent involved advanced persistent threats (APT) or sophisticated actors. Other actor types included hacktivists, insider threats, and criminals. In many cases, the threat actors were unknown due to a lack of attribution data.” states the report.
Analyzing incidents reported by sector, it is possible to note that the majority of the attacks involved entities in the Energy Sector followed by Critical Manufacturing. About 30 percent of the incidents hit infrastructures in the energy sector, meanwhile Critical Manufacturing (i.e. manufacturing of vehicles and aviation and aerospace components) accounted for 27 percent.
The threat actors used a significant number of zero-day vulnerabilities to compromise industrial control systems through the exploitation of web application flaws.
The most common flaws exploited by attackers include authentication, buffer overflow, and denial-of-service . Noteworthy among ICS-CERT’s activities included the multi-vendor coordination that was conducted for the ”
“Noteworthy among ICS-CERT’s activities included the multi-vendor coordination that was conducted for the “Heartbleed” OpenSSL vulnerability. The team worked with the ICS vendor community to release multiple advisories, in addition to conducting briefings and webinars in an effort to raise awareness of the vulnerability and the mitigation strategies for preventing exploitation” states the ICS-CERT report to explain the coordination activities sustained by the agency to address principal vulnerabilities.
The ICS-CERT MONITOR report confirmed that the attackers used a vast range of methods for attempting to compromise control systems infrastructure, including:
• malicious code designed to compromise air-gapped networks
• spear phishing attacks
• watering hole attacks
• SQL injection attacks;
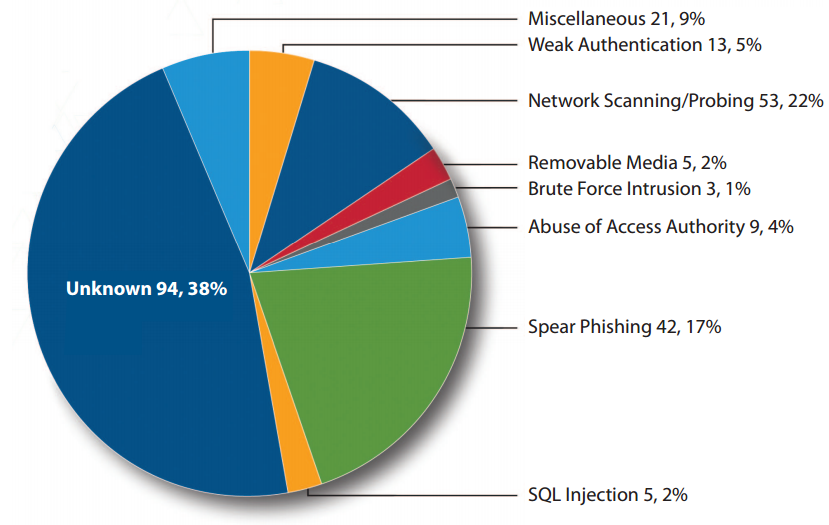
ICS -CERT Attack Methods
Unfortunately, it is quite difficult to attribute an incident to a specific threat actor. In the majority of cases, these offensives have gone under the radar over the years due to high level of sophistication of the Tactics, Techniques, and Procedures (TTPs).
The victims were not able to identify the threat actors. Neither the attack vector exploited by hackers for 38 percent of the reported incidents,
“Many more incidents occur in critical infrastructure that go unreported,” states the ICS-CERT MONITOR report. “Forensic evidence did not point to a method used for intrusion because of a lack of detection and monitoring capabilities within the compromised network”.
The experts analyzed the historical outages, estimating that currently the power interruptions, most of which last five minutes or less, already cost the US about $96 billion. The cost related to a prolonged outage is likely to be included in the range of $36 billion to $156 billion. The Commercial and industrial sectors are the sectors most impacted by the attack on the power grid due to their dependency on the electricity supply.
“Evidence from historical outages and indicative modeling suggests that power interruptions already cost the US economy roughly $96bn8 annually. However uncertainty and sensitivity analysis suggest this figure may range from $36b to $156b.” continues the report. “Currently over 95% of outage costs are borne by the commercial and industrial sectors due to the high dependence on electricity as an input factor of production.”
As explained in the report, it is important to identify the risks related to a possible cyber-attack and adopt all the necessary measures to mitigate them. The protection of critical infrastructure like a power grid is an essential part of the cyber strategy of any Government.
InfoSecInstitute: http://bit.ly/1DfQLlT


























