Edward Snowden Joins Twitter & Follows NSA
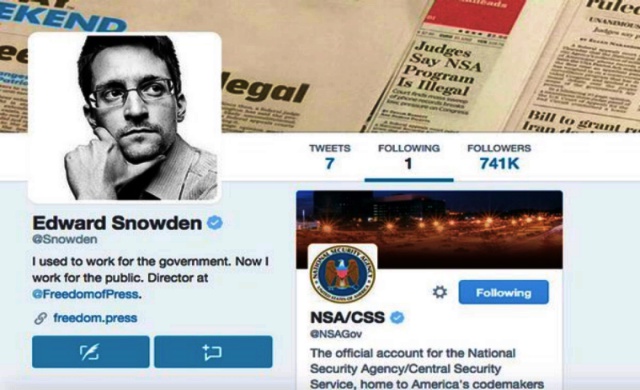
Now over a million followers.
Fugitive US intelligence contractor Edward Snowden has opened an account on the social network website Twitter.
His opening tweet was: "Can you hear me now?" In his profile, Edward Snowden says he "used to work for the government. Now I work for the public". He quickly gathered thousands of followers.
So far, Snowden, who is wanted in the US for leaking secrets, only follows one other Twitter user - the US National Security Agency (NSA).
He is believed to be living in Moscow where he is sheltering from US prosecutors.
In his second tweet - a reply to US astrophysicist Neil deGrasse Tyson - Mr Snowden joked: "Now we've got water on Mars! Do you think they check passports at the border? Asking for a friend."
And in another tweet he said: "Hero, traitor - I'm just a citizen with a voice." The @Snowden account was verified by Twitter and within nine hours of joining, Mr Snowden had accumulated more than 710,000 followers.
In June, former Olympian and reality TV star Caitlyn Jenner became the fastest person on Twitter to reach one million followers - in just over four hours.
Mr Snowden left the US in 2013 after leaking to the media details of extensive Internet and phone surveillance by US intelligence. His information made global headlines when the Guardian newspaper reported that the NSA was collecting the telephone records of tens of millions of Americans.
Mr Snowden is believed to have downloaded 1.7 million secret documents before he left the US. Although some consider him a traitor for his revelations, many others around the world say he is a champion of civil liberties.
In the US he faces charges that could put him in prison for up to 30 years.
Earlier this year, speaking via video-link to a Geneva audience, he said he would like to be granted asylum in Switzerland. He has previously worked in Geneva undercover for the CIA.
Regarding a possible return to the US, he told the audience that the authorities there had given him no assurances of a fair trial. "The only thing they've said at this point was that they would not execute me," he said. "That's not quite the same thing as agreeing to a fair and open trial."
BBC: http://bbc.in/1KQz49Z


























