Flash Player Attacked in Latest Cyber-Crime
According to FireEye, the security company, cyber-crooks are using attack tools aimed at Adobe Flash Player's obsolete editions and have created one exploit to abuse a security flaw, which Adobe patched on May 12, 2015. This is a development that gives rise to certain severe security problems.
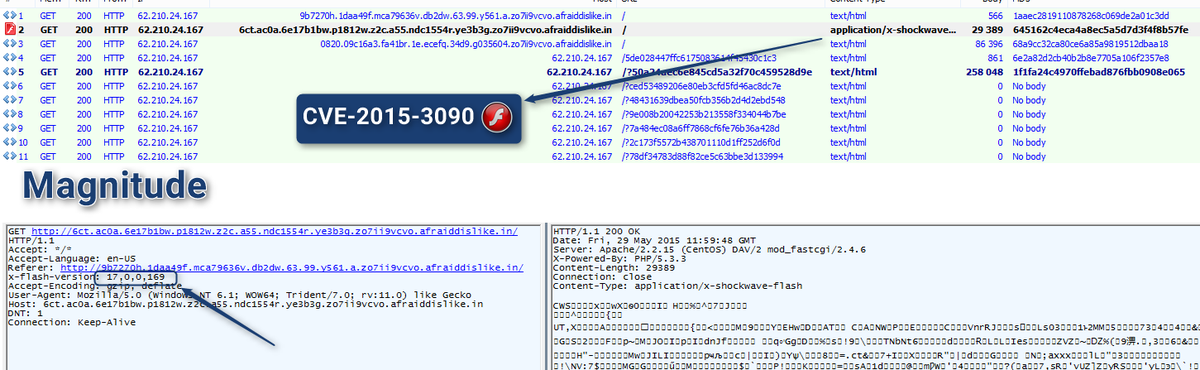
FireEye says the vulnerability mentioned is named CVE-2015-3090 as it represents one memory corruption bug that Google Project Zero's Chris Evans unearthed and reported.
The time Adobe issued the patch, it seemingly did not know about any assault, which abused CVE-2015-3090. According to FireEye, the exploit designed to manipulate the vulnerability associates with certain race situation within shader category where it changes certain shader object's height and width, so beginning any shader task would cause the memory corruption flaw.
Meanwhile, security investigators at FireEye noticed one malicious advertising campaign utilizing CVE-2015-3090 for serving the click fraud malware 'Bedep Trojan.'??Nevertheless, when the system is affected then aside executing ad-fraud activities, Bedep as well begins one infection schedule which ultimately introduces more malware.??
The malicious program requests harmful advertising networks numerous times and the networks divert traffic onto malevolent sites which carry on the linkage towards certain server having any of the Magnitude, Angler, Rig or Nuclear exploits kits.??
There is one particular Bedep referrer to each of the requests from where rapid diversions occur taking the Web-browser onto many domains one-by-one to reach the ultimate destination, investigators at FireEye elaborate. Softpedia.com reported this, May 27, 2015.?
During Angler's instance, a particular diversion occurred from one bogus news portal having "news4news" a string within its URL address.??According to investigator, over 220 Internet Protocol addresses were spotted that sub-domains having "click2" at the beginning of their URLs were utilizing for diversions.??
It's strongly recommended that users avoid the particular network, while maintain up-to-date perimeter security software containing the most recent defense features so exploit kit assaults can be prevented, FireEye concludes.
Spamfighter: http://bit.ly/1IfoJn3


























