Hackers Can Spy on Every Mobile
 Flaws in SS7 networks allow hackers to snoop, re-route calls and read text messages.
Flaws in SS7 networks allow hackers to snoop, re-route calls and read text messages.
There is a security hole in modern telecommunication systems that could be exploited by cyber criminals to listen in on phone conversations and read text messages. German hackers, based in Berlin, were able to intercept data and geo-track every mobile user by exploiting a flaw in the SS7 signaling system.
SS7 is a set of protocols used in telecommunications ever since the late 1970s, enabling smooth transportation of data without any breaches.
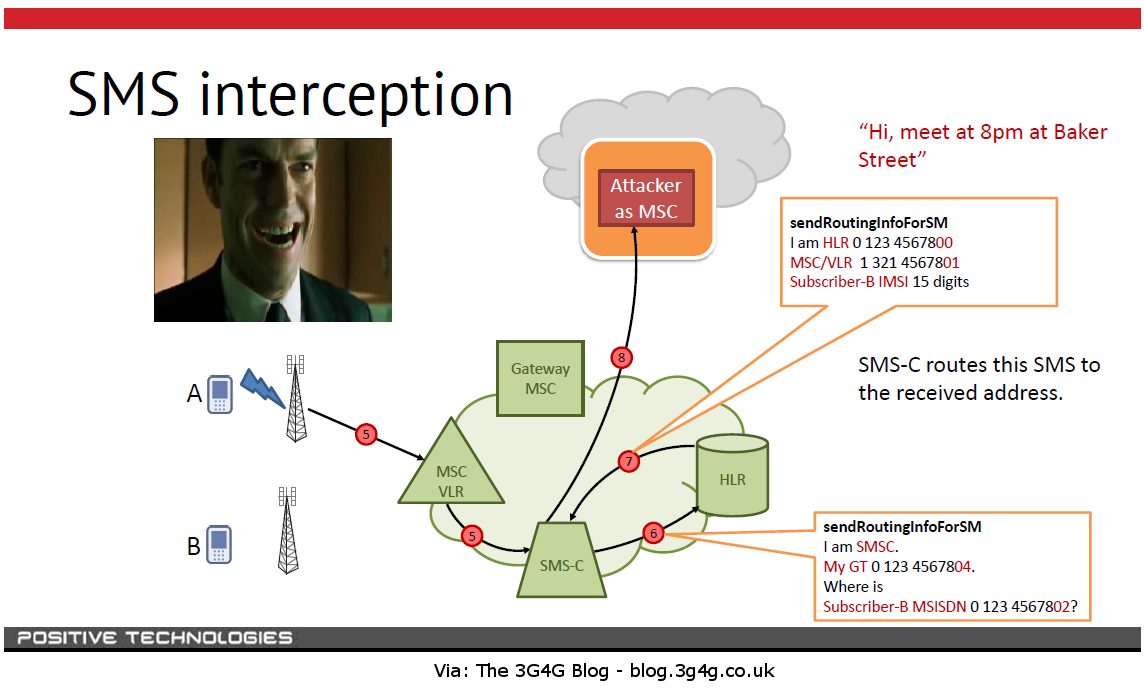
The SS7 protocol allows cell phone carriers to collect location data related to the user’s device from cell phone towers and share it with other carriers, this means that exploiting the SS7 a carrier is able to discover the position of its customer everywhere he is.
“The flaws, to be reported at a hacker conference in Hamburg this month, are the latest evidence of widespread insecurity on SS7, the global network that allows the world’s cellular carriers to route calls, texts and other services to each other. Experts say it’s increasingly clear that SS7, first designed in the 1980s, is riddled with serious vulnerabilities that undermine the privacy of the world’s billions of cellular customers.
The flaws discovered by the German researchers are actually functions built into SS7 for other purposes, such as keeping calls connected as users speed down highways, switching from cell tower to cell tower, that hackers can repurpose for surveillance because of the lax security on the network.” reports The Washington Post.
In the hacking community is known the existence of several techniques that hackers and snoopers can make use of, in order to eavesdrop and intercept phone calls or written text messages. In December 2014, German researchers have placed the matter to the public for consideration at the Chaos Communication Hacker Congress, since there can be a great many problems emerging.
Carriers of mobile telephony spend large amounts of money towards expanding their network and securing the conditions of communication with 3G and high-end encryption. To quote Tobias Engel, one of the German researchers mentioned above,
“It’s like you secure the front door of the house, but the back door is wide open”.
One of the major incidents registered by NKRZI (which is the National Commission for the State Regulation of Communications and Information in Ukraine) involved Russian addresses back in April 2014.
The expert noticed that many Ukrainian users of mobile phones have been affected by the notorious SS7 packets that is possibly derived from Russia. As a result, the mobile phone holders were intercepted of their address details and everything that was stored inside each phone. MTS Ukraine obviously participated in the interception, in relation to MTS Russia. As a direct consequence of security breaches related to SS7 protocols of telecommunication, the eminent threat is that of surveillance taking place between countries.
The system is being used by several major providers, meaning that data could easily be exposed to hackers. Names, addresses, bank account details and medical data stolen due to a security vulnerability that could give hackers the access to their mobile devices.
Unfortunately, the vulnerabilities into SS7 protocol will continue to be present, even as cellular carriers upgrade to advanced 3G technology to avoid eavesdropping.


























