Legality of Target Acquisition: The U.S. Needs a Drone Board
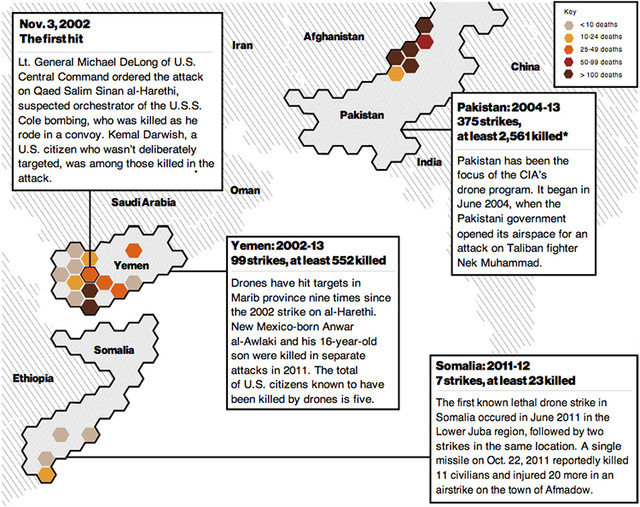
More than 3,000 deaths from the U.S. drone program worldwide are on the public record
Recently we learned that a US drone strike in Pakistan inadvertently killed an American and an Italian held as hostages by al Qaeda. The strike also killed a US citizen who was a prominent member of al Qaeda. A separate operation in January killed an American-born al Qaeda spokesman. The deaths of hostages Warren Weinstein and Giovanni Lo Portois are tragic and the Obama administration has pledged to conduct an independent review to understand how to prevent this type of grievous mistake. The apparently unintentional killings of two American al Qaeda operatives raise an additional question that President Obama did not address in his televised statement today: under what circumstances may the United States intentionally use targeted lethal force against a US citizen abroad?
The Obama Administration has previously considered the question; several years ago, Justice Department lawyers set out the legal rationale for targeting radical cleric Anwar al Awlaki, a dual Yemeni-US citizen, in a now-public white paper and redacted memo. Satisfied that Awlaki was a permissible target, President Obama authorized a CIA-led operation that culminated in drone aircraft, armed with Hellfire missiles, striking and killing the cleric in Yemen in 2011.
So why bother rehashing the question? For one, lawyers across the ideological spectrum have challenged the Justice Department’s legal reasoning. In particular, critics argue that secret and internal executive branch review, however painstaking and careful, does not satisfy the Fifth Amendment, which provides that no person shall be deprived of life without due process of law.
How it works now
The current scheme is rigorous, but insulated from outside review and accountability. Indeed, the ACLU filed a lawsuit last month seeking Obama administration documents that establish the criteria for placement on the “kill list” for the use of lethal force. Military and executive branch departments nominate, vet, and validate candidates for the “kill list,” considering the legality of each strike and potential operational impact. The nominations trickle up to the National Counterterrorism Center, or NCTC, and to the National Security Council, or NSC, before the President signs off.
Judicial Oversight
The US government concedes that the Fifth Amendment, in particular the Due Process Clause, applies to US citizens abroad. The Fifth Amendment establishes that “no person shall … be deprived of life, liberty, or property, without due process of law.” But due process does not always mean a trial in a federal court. As former Attorney General Eric Holder affirmed, “‘Due process’ and ‘judicial process’ are not one and the same, particularly when it comes to national security.” But if a person does not receive a federal court trial to determine whether the government can take away his life, how do we know whether the process he received is the process he is due?
Critics of the Obama Administration’s targeted killing program began recommending greater oversight and judicial review of the decision-making process early in President Obama’s first term. Though Justice Thomas and others scoffed at the notion of a “drone court,” the idea gained traction in policy circles. Some academics have also endorsed the idea of a “drone court,” in which federal judges would undertake a prior review of targeting decisions, in many cases using the Foreign Intelligence Surveillance Court as a model.
Notwithstanding the support for a drone court, prior review of the President’s targeting decisions by federal judges is not likely to succeed. Perhaps the most significant impediment is constitutional. Granting authority to the judiciary to regulate the president’s conduct of war would limit the President’s constitutionally afforded power as Commander in Chief of the military, thus raising serious separation of powers concerns.
Recognizing the difficulties that prior review by federal judges poses, some scholars have called for judicial review after a targeting operation.
Other proposals call for prior review by executive branch officials, or as Georgetown law professor Neal Katyal puts it, a “‘national security court’ housed within the executive branch itself.” However, a military review board is unlikely to be a neutral body when reviewing military intelligence and decision-making. A binding decision would impermissibly constrain the President’s Commander in Chief power. A “national security court” would also be viewed as biased because the President’s own national security advisors, the same people who vet the kill list, would serve as adjudicators. Despite the drawbacks of these proposals, they may be on to something.
A New Model
As a way to provide due process to US citizens, enable accountability for targeting decisions, increase public trust in the decision-making process, and avoid the use of excessive or erroneous force against targets, we propose an executive branch board (Drone Board) that would conduct a prior review of the use of targeted lethal force against U.S. citizens abroad.
The growing risk that US citizens will join terrorist groups around the world and be targeted for killing overseas by their own government creates an imperative to resolve when and how the U.S. government may lawfully use lethal force against its own citizens abroad. A Drone Board would be an important step to provide additional process and greater public confidence in the method of targeting US citizens overseas.
DefenseOne: http://bit.ly/1Us02wV


























