Baltimore Police Use ‘Stingray’ Cellphone Surveillance
US Baltimore Mayor Stephanie Rawlings-Blake defended the widespread use of a cellphone surveillance device that sweeps up phone signals, echoing the Baltimore Police Department's stance that it's used to track criminals and limited in the type of data it collects.
Kevin Harris, a spokesman for Rawlings-Blake, said the mayor was aware of the program and supports it as an "effective tool" that has proved useful for police departments across the country. Nonetheless, Harris said, the mayor is open to discussing ways to make the program more transparent.
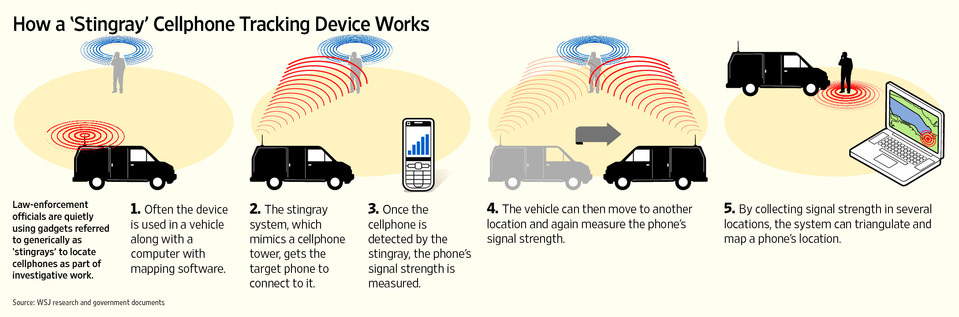
How a stingray device works:
Baltimore Police used secret technology to track cellphones in thousands of cases and the extent of Baltimore police's use of the so-called stingray device was largely secret until this week, when a detective testified in court that the department has used it 4,300 times since 2007 and that a 2011 nondisclosure agreement with the FBI prevented police from discussing details about it.
As part of the agreement, the FBI retains the right to ask local police departments and prosecutors to drop cases against criminals before revealing information about stingray programs.
The stingray has come under scathing criticism from privacy advocates. Christopher Soghoian, a technology expert with the American Civil Liberties Union, said focusing on ways the stingray aids police investigations disregards the indiscriminate collection of phone signals and the device's ability to jam phone service in areas where police use it.
Soghoian said the shroud of secrecy surrounding stingrays leaves judges in the dark about the type of police operations they are allowing and law-abiding citizens unaware of their vulnerabilities to such technology. He also noted that enough information is already publicly available for criminals to create their own stingray-like tools.
City Councilman Brandon Scott said he understands why police did not disclose its widespread use until recently. "We all know if they make an agreement with the federal government, they need to honor that agreement," he said.
Still, Scott said he wants assurances that police are not tracking the phones of individuals not involved in criminality.
Such devices act as mobile cellphone towers, forcing phones within a certain radius to connect to them and share their unique identifying information. That information allows police to track the location of a targeted phone.
The technology is increasingly being used by local law enforcement officers and is used at the national level, by the US Marshals Service for surveillance planes. Members of Congress and the ACLU have been pressing for more information about the devices and asked the Federal Communications Commission to look into their use.
Rep. C.A. Dutch Ruppersberger, a Maryland Democrat, said that he has asked the FBI for "greater clarification" about how the device is deployed. Sen. Chuck Grassley, an Iowa Republican and chairman of the Senate Judiciary Committee, said there should be reporting on how often the technology is used, under which legal authorities, and what independent audit controls are in place to prevent abuse.
Baltimore Sun: http://bsun.md/1JMxbNh


























