How To Hack a Military Drone
Recently published research has given hackers a manual for breaking into unmanned systems, according to an Israeli defense company.
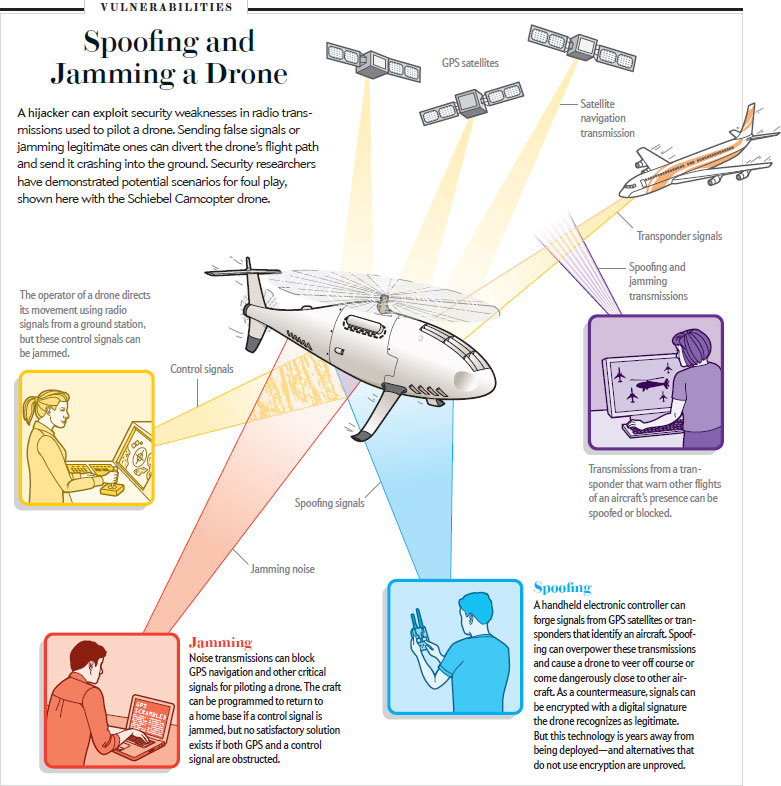
A downing of a CIA stealth drone by Iranians occurred a month after one such paper was published (entitled - The Requirements for Successful GPS Spoofing Attacks) noted Esti Peshin, director of cyber programs for Israel Aerospace Industries, a major defense contractor. In December 2011, the Christian Science Monitor reported that Iran navigated a CIA unmanned aerial vehicle safely down to the ground by manipulating the aircraft’s GPS coordinates.
The 2011 study, co-authored by Nils Ole Tippenhauer of ETH Zurich and other ETH and University of California academics, detailed how to mimic GPS signals to fool GPS receivers that aid navigation. “It’s a PDF file… essentially, a blueprint for hackers,” Peshin said.
Peshin said she does not know whether the CIA drone was overtaken using GPS spoofing or even whether the attacker read the study. But she underscored how easily available the publication is online.
In the study, the researchers explained where an attacker must be located to generate fake signals capable of fooling GPS receivers. They also described ways to replace legitimate signals with an attacker’s bogus signals, so the target ends up ”losing the ability to calculate its position.”
The authors of the Swiss study offered some advice on how to neutralize GPS deception, for instance, by hiding the exact positions of GPS receivers. Their intention was not to aid and abet terrorists, but rather to highlight “effective receiver-based countermeasures, which are not implemented yet in current standard GPS receivers,” the researchers said.
While the academics did not mean any harm, hackers could have quickly exploited their instructions before vendors had time to fortify satellite-guided vehicles, Peshin said.
The Pentagon is currently working to insulate UAV navigation and surveillance from outside interference. Specifically, special software on a forthcoming hacker-proof Boeing Little Bird helicopter drone would shield communications from tampering.
DefenseOne: http://bit.ly/1IvdbzW


























