HTC: Rendered Worthless By Insecurity?
Fingerprint biometrics unencrypred: attackers can sit in the background and collect the fingerprint image of every victim.
Internet hyperbole (and financial analysis) has rendered HTC, a once high-flying mobile brand, essentially valueless.
In short, the company is trading below cash on hand. So if you bought all HTC stock, the company would have to pay you, the buyer, to take it over. This means the company’s factories, stock and brand are worth nothing, at least on Wall Street.
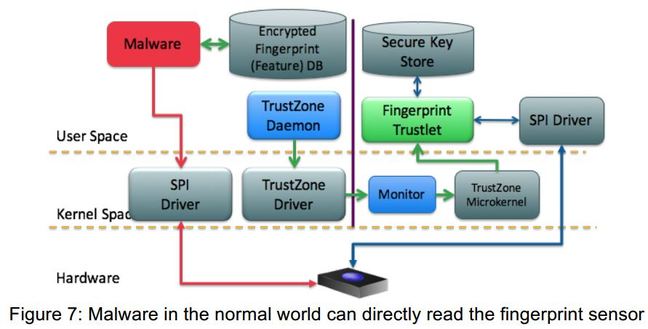
Furthermore, the researchers have discovered that the HTC One Max has been keeping fingerprint biometrics used to unlock the cellphones in an unencrypted “world-readable” file, a definite no-no in the world of security. Hackers could easily open the file /data/dbgraw.bmp on the phone’s memory and capture your fingerprint data.
It is clear that companies like HTC and Samsung are about to be hit by lower-end manufacturers right where it matters most: price. The profit on an average Android phone is about a penny. This means the only way to survive is by reducing the price of a phone as much as possible. However, the modern phone marketers like Samsung and HTC only want to sell flagships – big, tent-pole phones that lend themselves to big marketing budgets and fancy commercials.
There is no perceived upside in flogging the cheapest of the cheap, especially considering the “fanciest” phone out there is the iPhone. When your only competitor is also ostensibly the most expensive phone on the market, there is little value in highlighting your cheapest models.
When HTC first began selling its own phones in about 2006, the market was wildly striated. There was a solid base of “free” phones running a Java stack that offered little more than a keypad and a contact list.
In the mid-range were clever feature phones like the HTC Wizard and Samsung Blackjack that appeared every few months and were aimed at a general “upgrader” class of user who wanted little more than to have the latest cell phone.
Finally, there were the luxury phones like the iPhone and a few Galaxy phones, as well as business-focused brands like BlackBerry and even LG with its crazy Prada phone. These price points allowed for a certain amount of cushion as cell phone newbies picked up cheap phones and the die-hards paid a premium for the good stuff.
Now it’s iPhone and everyone else. The cell phone buyer’s market is saturated. Even the upgrade cycles have grown longer. In short, people are holding onto their expensive phones longer or buying wildly cheap ones. There is no middle ground.
HTC got hit with a one-two punch this week. The financial news and the security discovery are exactly the pieces of information that will further drive HTC’s stock price – and popularity – into the toilet. HTC might be able to pull a Motorola and partially pull out of the nosedive, but, knowing the market for the average cell phone, I’m not holding my breath. Too many cell phones and too little profit make for a really bad business.
Techcrunch: http://tcrn.ch/1gFUgrr


























