ICWATCH Database Gathers the CV’s of 27,000 Intelligence Employees
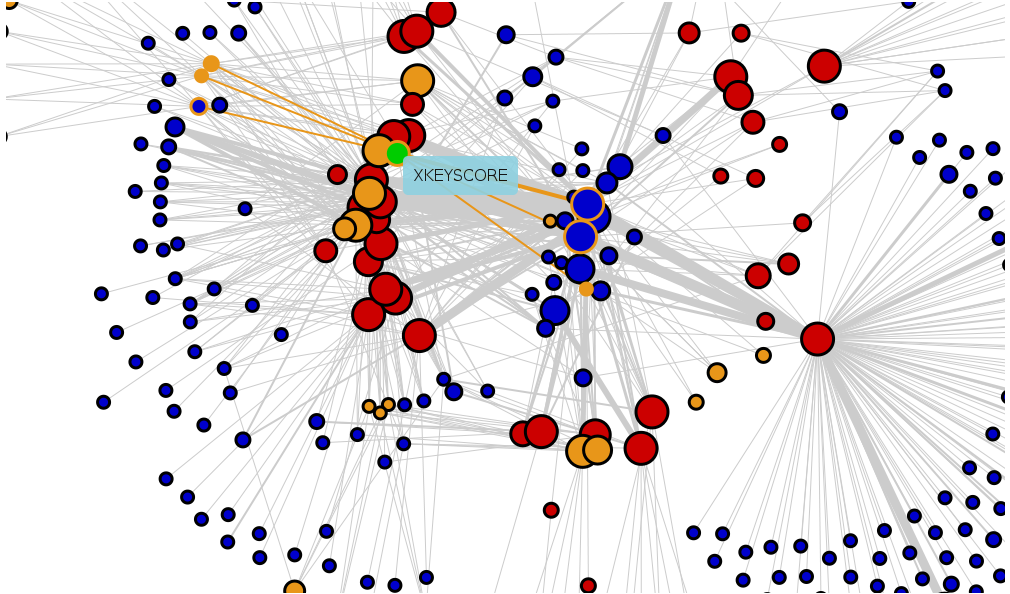
Network graph generated with Transparency Toolkit
Surveillance is usually a one-way street. As the NSA and its partners monitor Internet traffic, read peoples’ emails, and analyse phone metadata, the public rarely gets an insight into the people who actually carry out this work. Now one project is trying to change that, with the release of a database containing the LinkedIn profiles of over 27,000 people working in the intelligence community.
The “ICWATCH” database—a play on the NSA data-sharing program ICREACH—was developed by Transparency Toolkit, a group focused on working with open data, and was presented at the tech and policy festival Republica in Berlin. The purpose of collecting all of these profiles, according to the project website, is so “that people can use them to better understand mass surveillance programs and research trends in the intelligence community.”
The database can be searched by company, location, industry and a host of other parameters, and plenty of results also include a portrait photo of the intelligence community member. The Transparency Toolkit collects and analyses all sorts of open data, such as online resumes, job listings, and social media—“and we use that to understand surveillance programmes, primarily, and also human rights abuses,” MC McGrath, who worked on ICWATCH with Brennan Novak and Kevin Gallagher, told me over an encrypted phone call.
But for this particular intelligence community-focused project, they focused mostly on LinkedIn.
Shortly after whistleblower Edward Snowden’s revelations, it became apparent that many people within the intelligence community were listing the code names of top secret surveillance programmes on their LinkedIn profiles. As publicly available data, these were easily discoverable by a basic Google search. McGrath, after successfully finding some profiles himself, thought about automating this process and seeing what it would reveal.
The tool his team developed searches for code names, intelligence agencies and departments, and various technical terms. Some of those keywords are already well-known, such as XKEYSCORE, the name of an NSA system that purportedly collates data such as emails and browsing histories. Some journalists also told McGrath what terms they would like to search for.
The search returned a mountain of results, and even picked up on people who allegedly work for Tailored Access Operations (TAO), the elite hacking unit of the NSA suspected of hacking into systems all over the world.
But, “Most of the people posting on these profiles are not in the NSA themselves,” McGrath pointed out. Instead, they work for contractors, such as Booz Allen Hamilton, where Snowden previously worked, or Lockheed Martin. Some profiles provided more information about specific surveillance programmes. One, codenamed “PENNANTRACE”, was found on the profile of a Senior SIGINT operator (SIGINT means “signals intelligence”, which is the monitoring of communications or signals). Based on what he found, McGrath thinks PENNANTRACE is connected to the use of surveillance drones, he told me. One job description found on LinkedIn described PENNANTRACE as an “airborne collection platform”.
“There are lots of things openly available in job listings and social media about this, but there’s not anything publicly released,” he said.
McGrath also came across a series of trends to do with employment in the intelligence community. The number of people claiming to work with SIGINT databases, for instance, has increased dramatically over the years since 2008, with just a small decline starting in 2013.
“It’s interesting to watch the trends of when people start working on certain programs, or when the intelligence community grows, based on LinkedIn data,” he said.
And then there’s the human element: This research has shown who is actually working within the intelligence community, something that is naturally shrouded in secrecy.
“I think they’re, for the most part, pretty normal people,” McGrath said. “They had Facebook profiles, they had various pictures, funny pictures.”
In his presentation, McGrath displayed a series of photos found through his automated search of LinkedIn. Some of the more personal photos—a family holiday snap, for instance—were taken manually from Facebook profiles that McGrath tracked down himself. “I’m yet to automate that part, but maybe eventually I’ll have something that matches up Facebook profiles with people on LinkedIn,” he said.
McGrath told me that before embarking on this project he did consult with a number of lawyers.
The point of all this was to better “understand the intelligence community,” McGrath said, but also to draw attention to “some of the individuals involved.”
When asked whether anybody on this newly created database had contacted him, McGrath replied, “I haven’t heard from any of them yet, but it’s possible that I will.”
Motherboard: http://bit.ly/1J0GAyj
Transparency Toolkit: http://bit.ly/1LSFLh9


























