Spy Agencies Go Recruiting on LinkedIn
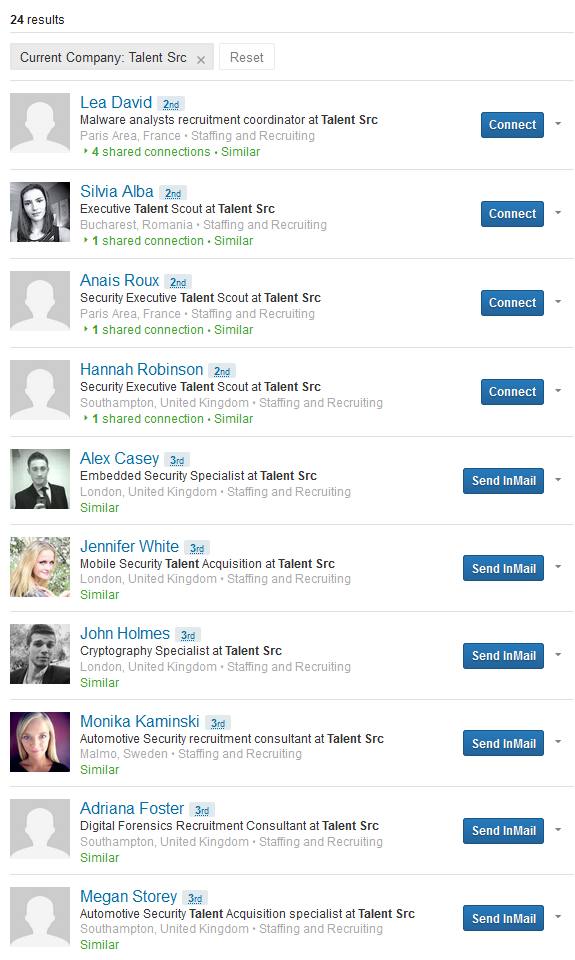
F-Secure analysed bogus LinkedIn accounts to discover that they belong to individuals supposedly working for Talent Src (Talent Sources).
MI5 have warned that ‘hostile intelligence services’ are clandestinely targeting Government employees through the popular online CV website. Secret agents working for malign foreign powers, including Russia and China, have created fake profiles on the social networking service to lure unsuspecting victims.
In the elaborate scam, that wouldn’t be out of place in a James Bond novel, enemy spies are using bogus accounts on the website, described as like Facebook but for business professionals, to try and ‘find, connect with, cultivate and recruit’ current and former Government employees. Instead of a trusting civil servant connecting with a potential business partner, they are unwittingly tricked by a foreign agent into exposing a treasure trove of personal details, including pictures, phone numbers, email addresses and information about their work in Whitehall.
Security experts have said that even current members of Britain’s spy agencies, MI5, MI6 and GCHQ, have put potentially risky information in LinkedIn profiles. Others on the website work, or were previously employed, in departments which deal with highly-sensitive intelligence such as the Foreign Office, Home Office or Ministry of Defence. Now spy chiefs have launched a crackdown to minimise the threat of enemy agents coaxing out secrets.
In a document sent by email on July 24, MI5 announced a ‘Security Service Espionage Alert’. Containing the MI5 logo, the missive identifies a string of ‘key points’. In July 2009, the new head of MI6 Sir John Sawers’ personal details were plastered over Facebook. These include the warning that ‘Hostile foreign intelligence services are increasingly using LinkedIn to find, connect with and begin cultivation and recruitment of current and former HMG [Her Majesty’s Government] employees.’
It adds: ‘MI5 investigations have identified a large number of HMG employees connected to known hostile foreign intelligence service cover profiles.’
The document, circulated in Whitehall, provides ‘advice to help you protect yourself online and what to do if you think you may have been the subject of an approach.’
LinkedIn, which was founded in December 2002, has more than 364million users in 200-plus countries.
Professor Anthony Glees, of the University of Buckingham’s Centre for Security and Intelligence Studies, said last night: ‘An enemy agent who might know he is a spy would be able make deductions from that about what our intelligence agencies are interested in at the moment.
‘What people don’t understand is that social media is used as a tool for intelligence gathering not just by us but by other countries who are hostile to us.'
Russia, along with China, has been accused of mobilising a huge cyber-spying operation targeting the UK and other nations. Security sources have warned that Moscow and Beijing routinely seek to steal military secrets from government and major defence contractors.
MI5 has repeatedly warned that it is tackling ‘industrial-scale’ cyber-attacks from both hostile countries, terrorists and organised gangs.
In March 2013, NATO’s most senior commander was embroiled in a major security alert after a fake Facebook account was set up in his name by suspected Chinese spies. Senior British military officers and Ministry of Defence staff are understood to have accepted ‘friend requests’ from a bogus account for Nato’s then Supreme Allied Commander James Stavridis.
In the mistaken belief they had linked up with the American admiral on social media, they then unwittingly provided a vast trove of personal details. And in July 2009, the new head of MI6 Sir John Sawers’ personal details were plastered over Facebook.
Shortly after being appointed, his own security was breached when his wife posted photographs on Facebook showing him in tight fitting swimming trunks, along with details about where Sir John’s family live and work, and where they spend their holidays. In an embarrassing blunder for MI6, millions of people could have gained access to compromising photographs of Sir John Sawers and his family on the social networking website.
Mail: http://dailym.ai/1FX1CNL


























