Why Is China Hacking Norway?
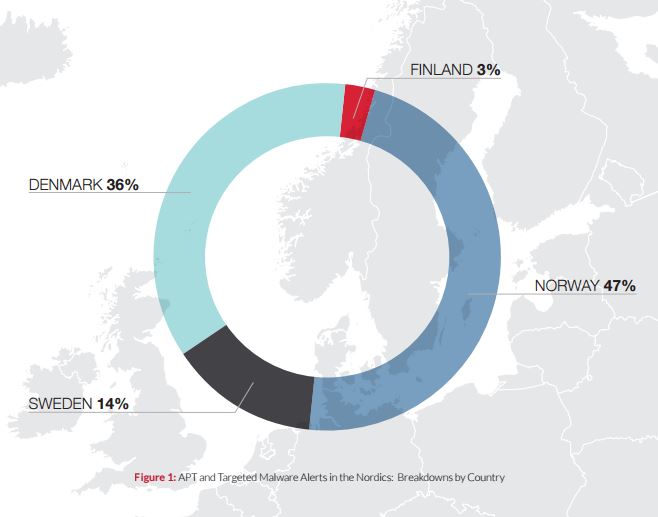
The FireEye analysis of threat activities revealed that the highest number of APT and malware alerts were observed in in Norway (47%), followed by Denmark (36%), Sweden (14%), and Finland (3%).
All states spy. Stealing corporate secrets and understanding what other governments are thinking and planning have often been important methods for states to get ahead of their competitors.
This May, the cyber-security company FireEye released a report on cyber-espionage aimed at the Nordic states. Some of the report’s key findings were hardly surprising. Russia and China were the two states from which most cyber-attacks originated. Defense/aerospace, energy and high-tech communications are the industries, which have been the most targeted by cyber intrusions from these two states. Considering the Nordic states’ advanced, often niche, research and development within these sectors, that’s not surprising.
However, there was also quite a lot of activity aimed at acquiring classified government and military memos and emails. While this is to be expected from Russia, considering its position vis-à-vis NATO (of which three out of the five Nordic states are members, Sweden and Finland being the exceptions), it’s interesting that Beijing is showing an interest in a region from which it is so far removed.
Interestingly, out of the five Nordics, Norway was the country which had been most targeted by cyber intrusions. In fact, almost 50 percent of all intrusions in the Nordic states were aimed at Norwegian companies. Norway also seems to be the main target of hackers based in China.
Norwegian offshore energy and defense were the most targeted sectors by attacks emanating from both Russia and China. Russia is investing heavily in Arctic oil and gas and advanced Norwegian offshore tech would definitely be useful for that purpose. Chinese hackers were apparently also interested in Norwegian energy tech. China has its own interests in developing hydrocarbons in the Arctic, as well as boosting its own capabilities via offshore oil extraction elsewhere. Furthermore, gaining information on planned concessions on Norwegian offshore oilfields would be of interest to Russian and Chinese companies that are planning on investing there.
Meanwhile, Norway has an advanced and, for a country of its size, relatively large defense industry. It largely fills a niche for NATO, developing and producing missiles and sensors. One project which might be particularly interesting to both Chinese and Russian militaries is the Naval Strike Missile/Joint Strike Missile (NSM/JSM), developed as a joint project between Norwegian arms company the Kongsberg Group and U.S. firm Raytheon. The United States and several other NATO countries have expressed interest in acquiring this missile, which is, according to Kongsberg, the only anti-ship missile which can fit inside the F-35 Joint Strike Fighter’s internal bays. Specs on this weapon will undoubtedly be of great interest to both Beijing and Moscow.
Beijing’s attempts to access classified government files and emails also merit scrutiny. Russian intrusions have also targeted government files, but this is less surprising considering Norway’s position as NATO’s “Northern Flank,” and the current tensions between NATO and Moscow in Ukraine.
The main motives behind China’s cyber-attacks are probably twofold.
First, Beijing has effectively thrown Oslo into the diplomatic deep freezer since the Norwegian Nobel Committee awarded the Peace Prize to Chinese dissident Liu Xiaobo. The CCP is probably interested in having some warning if a similar move will happen again.
Second, China is attempting to strengthen its own position in the Arctic. Beijing is eyeing the economic possibilities that might appear with the receding of the Arctic ice-shelf. Earlier this month, a PLAN squadron was spotted for the first time in the Bering Strait, perhaps an indicator of China’s interests and intentions in the region. Knowing what other Arctic actors are planning, especially one with which China has an antagonistic relationship, is definitely of interest to China.
The advent of cyberspace has only made it easier for states to follow the cardinal rule of espionage: don’t get caught. The ironic thing about espionage is that, once discovered, it often reveals quite a bit about the spying state’s intentions and anxieties.


























