Autonomous Submarine Drones: A Threatening New Weapons Platform
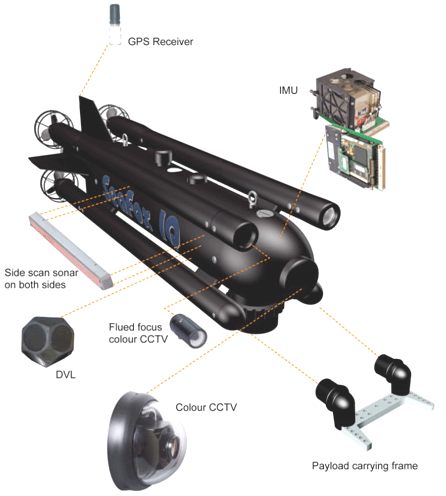
ATLAS ELEKTRONIK - Seafox Minehunting and Autonomous Underwater Vehicle (AUV)
Already, the US and other militaries are doing research into ways armed robots could do much of the work that is today performed by manned warships and submarines, especially in difficult environments like the Arctic.
But a new white paper from the United Nations Institute for Disarmament Research, released last month, warns that ever-smarter naval robots could make for very choppy waters in places where the United States, Russia, and other nations have a growing presence and competing interests.
“Experts have suggested that fully autonomous weapon systems are likely to first appear in the relatively ‘uncluttered’ maritime environment,” the report says. “While a small group of experts are actively considering the legal and ethical issues raised by maritime autonomy, policy-makers have directed little attention to the specific issues and challenges that arise in this context.”
Sea Monsters of the Future
While Elon Musk and others debate the logic of more autonomous aerial drones, the US Navy has long used autonomous weapons on its ships. The need for a sea system that could shoot on its own was evident to military leaders as far back as the 1950s, when advances in electronics and missile propulsion raised the prospect of highly accurate anti-ship weapons that could strike faster than human reflexes could defend. In the 1980s, US Navy ships began to install the Phalanx Close-In Weapons System, a radar-directed Gatling gun with an autonomous mode. In 2004, the Navy deployed a system called the Aegis Ballistic Missile Defense, capable of automatically finding and firing upon incoming ballistic missiles across an entire region. When missiles are streaking toward your destroyer at a thousand or more miles an hour, who has time for human reflexes?
Other naval forays into autonomy include the MK-60 CAPTOR submerged torpedo launcher, which can listen for enemy submarines — even waiting until a specific sub happens by — and pull the trigger automatically. Designers have also engineered a growing array of undersea robots for surveillance and mine hunting. In 2003, the US became the first nation to deploy an autonomous robot to look for submerged mines, near Iraq’s port of Umm Qasr.
While the Reaper gets most of the press, its waterborne cousins are currently evolving more quickly along the spectrum of autonomy. Last year, the Navy tested a swarm of 13 small robot boats on Virginia’s James River. They were able to maneuver in concert with one another to protect a target ship from enemy boats with almost no human direction.
The military is also working on a 132-foot robotic ghost ship that can follow diesel-powered submarines around the globe while also obeying the world’s nautical laws. And the Defense Advanced Projects Research Projects Agency, or DARPA, is developing a “world-wide architecture” of robot sea pods. Somewhat like mines, they would sit on the ocean floor—possibly for years—until commanded to deploy their payloads — possibly a drone, or some other weapon. “Today, the U.S. Navy puts capability on the ocean floor using very capable but expensive submarine platforms. What we would like to do in this program is pre-position capability on the ocean floor and have it be available to be triggered in real-time when needed,” DARPA deputy director Steven Walker said in March.
The need for autonomy is dictated by the isolated conditions under which naval drones may operate. Whereas the Predator or Reaper rely on the Global Positioning System, most underwater vessels can’t pick up GPS. A greater level of autonomy, in many instances, isn’t just an asset but a necessity of basic operation. That’s especially true for systems built to stay in the water for years at a time.
Just as militaries are working to establish a more permanent presence at sea, especially in today’s contested waters in the Pacific and Persian Gulf, they’re also looking to do so in newly accessible waters northward. Here’s where armed naval robots, the competing interests of naval powers, and an absence of clear law could be explosive.
“Many of the world’s conflict flashpoints are on coastal or contested waters. With rising seas, changing weather patterns, and other consequences of global warming, access to previously impassable areas will render the maritime environment an increasingly strategic battlespace for an ever-growing number of States,” the report says.
Case in point: President Obama visited Alaska last week to highlight the Arctic region’s growing economic importance, and discuss the impacts of climate change. A warmer Arctic has less sea ice coverage during the summer, allowing more shipping, fishing, and, especially oil development — which perpetuates the burning of fossil fuels, which causes a warmer Arctic.
Russia, which claims most of the oil rights under the Arctic Circle, has taken to bellicose assertions of its dominance in the region, like planting a flag under the North Pole. Meanwhile other Arctic states are getting itchy under their parkas.
As Obama was helping salmon to spawn, five Chinese warships were sailing the nearby Bering Sea. Meanwhile, Russia’s foreign minister sent a claim to the U.N. for 1.2 million square kilometers of Arctic sea shelf, citing “Ample scientific data collected in years of Arctic research.” In other words, the ability to access the Arctic, explore it, and document the process is all a part of making a legal claim to it. Autonomous underwater systems play a role in all of those processes.
In 2014, Denmark appealed to the United Nations for 900,000 kilometers of the Arctic seabed, a claim that conflicts with rival assertions by Canada and Russia. That same year, Canada began to test its military drones in Arctic conditions. “The project team deployed vehicles into situations that might be dangerous or difficult for a Canadian Armed Forces responder at a remote location to support search-and-rescue and hazardous-material operations,” said Simon Monckton, the mission’s lead scientist.
The United Nations report makes no clear recommendations for fixing increased autonomy in naval weapons except to ask: Do “increasingly autonomous technologies in the maritime environment require the development of a fundamentally new set of categories, concepts and rules?”
The answer, clearly, is yes. But as with climate change, new rules may not be enough to change the rising temperature.
DefenseOne: http://bit.ly/1glYK67


























