Cyber Insurers Won’t Cover Data Breach
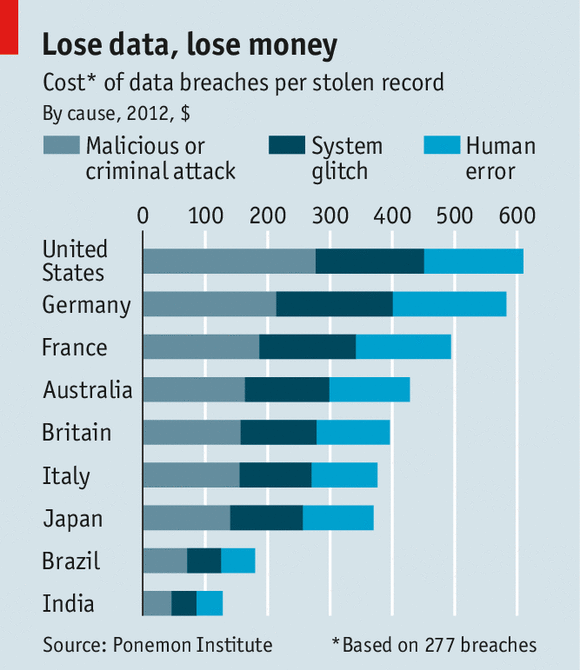
After Ponemon Institute’s report highlighted insurance protection as a way to mitigate the risk and consequences of a data breach, I’m sure some CEOs out there breathed a sigh of relief. “Great, we can just get cyber insurance and not have to worry about actually being cyber secure.”
Wrong!
Insurance protection is just one of the ways to mitigate costs; you must also consider having an incident response plan and team in place, extensive use of encryption, business continuity management involvement, CISO leadership, employee training, board-level involvement, and other factors.
Insurers can decline to pay out over inadequate cybersecurity.
Recently, California health care provider Cottage Health System awoke to news when their insurer declined to pay out for their data breach back in 2013 because they had failed to follow, “minimum required practices”. Specifically, the insurer is claiming that Cottage “stored medical records on a system that was fully accessible to the Internet but failed to install encryption or take other security measures to protect patient information from becoming available to anyone who ‘surfed’ the internet.”
Failing to implement basic cybersecurity measures will almost certainly mean that your insurance brokers won’t cover you. Considering the average cost of a data breach is now $6.5 million, this is a hefty price for any organization to pay out.
Basic cybersecurity practices:
Check your insurance policy carefully, but generally you’ll need to make sure you have these fundamentals of basic cybersecurity right.
Download software updates. It sounds like a no-brainer, but it is amazing how many viruses exploit outdated software. Use strong passwords. That is, passwords that contain a mix of lower- and upper-case letters, numbers, and symbols. And don’t leave your passwords lying around for everyone to see!
Don’t open suspicious emails. As we regularly report on this blog, a staggering number of phishing emails are sent every day. You need to be aware of these scams and ensure that you and your staff do not click on malicious links.
Use antivirus software.
Train your staff. People are your weakest security link – fact. Cyber criminals look to exploit the human fallibility or curiosity. For all the cybersecurity you have in place, one ill-advised click can undo all of your hard work. Staff awareness training is essential to successful cybersecurity.
Encrypt your systems and mobile devices. Don’t make a hacker’s job easier than it already is! In fact, if you implement robust cybersecurity measures, you will not only reduce your chance of suffering a data breach in the first place, but your insurance premiums will be considerably lower, too.
Implementing an information security management system (ISMS) aligned to ISO 27001 is considered to be the most comprehensive approach to effective cybersecurity. Recognized worldwide, ISO 27001 covers technical testing, incident response, bring your own device (BYOD) policy, risk assessments, and many other areas to ensure the confidentiality, integrity, and availability of your information that no other standard or framework can offer. ISO 27001 registration instills confidence in your clients and stakeholders that you take information security seriously, often winning you new business and strengthening existing partnerships.
It Governance: http://bit.ly/1BqrzIs


























